Key Features
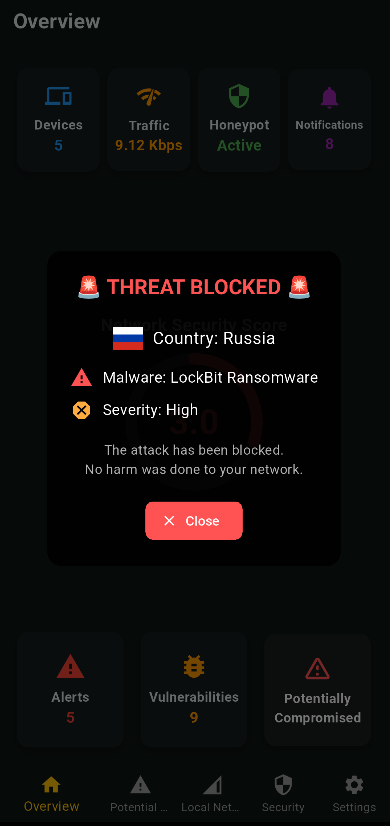
AI-Powered Network Defense
TRIANGULUS continuously scans your network, leveraging advanced AI-driven algorithms to detect and neutralize cyber threats in real time. Whether it's malware infiltration, unauthorized access attempts, or emerging attack patterns, our intelligent system identifies potential risks before they escalate. By automating the response to security incidents, TRIANGULUS ensures that your network remains protected around the clock with minimal user intervention.
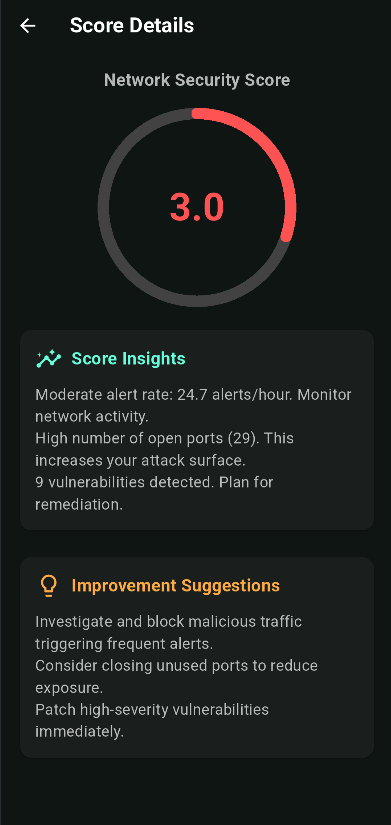
Real-Time Network Security Score
Stay informed about your network’s security health with TRIANGULUS' AI-generated security score. By analyzing real-time threat intelligence, system vulnerabilities, and active security protocols, the platform provides a comprehensive assessment of your risk level. More than just a number, this score comes with clear, actionable recommendations to strengthen your defenses, helping you proactively mitigate risks before they turn into security breaches.
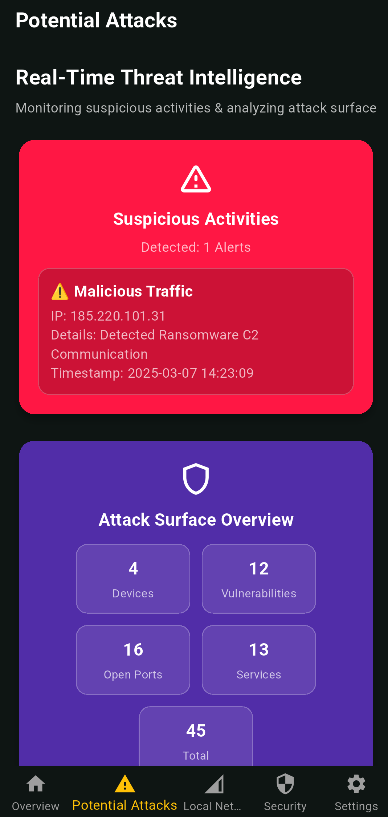
Device Security
TRIANGULUS continuously monitors all connected devices, assessing them for vulnerabilities and potential security risks. By scanning for outdated firmware, misconfigurations, and known exploits, the system identifies weak points before they can be exploited by attackers. Users receive real-time alerts along with tailored recommendations to patch vulnerabilities and enhance overall security, ensuring a proactive defense against cyber threats.
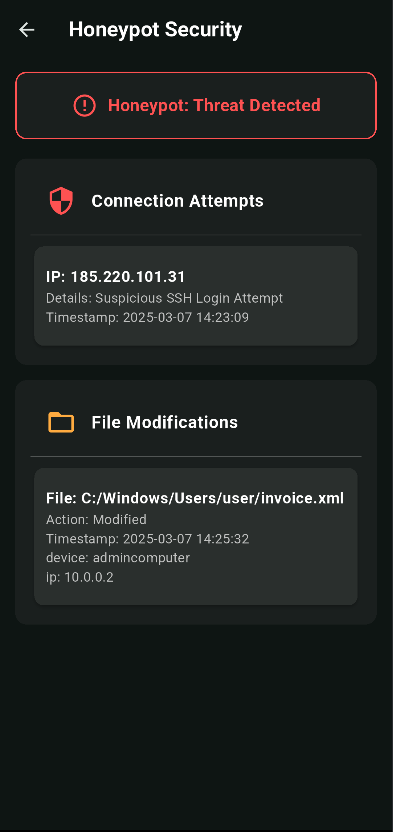
Smart Honeypot Technology
Using sophisticated deception techniques, TRIANGULUS deploys honeypots—network traps designed to lure and expose attackers. These strategically placed decoys imitate valuable network assets, tricking cybercriminals into revealing their tactics while keeping your actual systems safe. By analyzing these interactions, TRIANGULUS gathers critical intelligence on attack methods, strengthening overall security and preventing potential breaches before they occur.
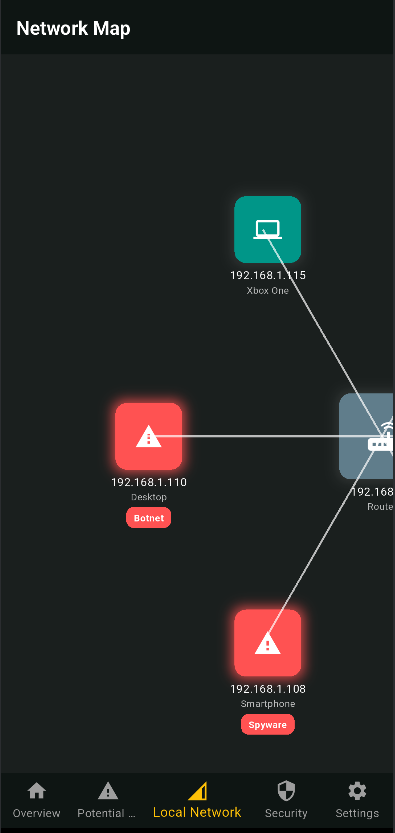
Interactive Network Map
Gain complete visibility over your network with TRIANGULUS' interactive real-time network map. Instantly see all connected devices, their security status, and any detected vulnerabilities in an intuitive, visual layout. Whether identifying unauthorized devices, monitoring active threats, or assessing network performance, this dynamic map provides a centralized view of your digital environment, empowering users to take swift action to secure their network.